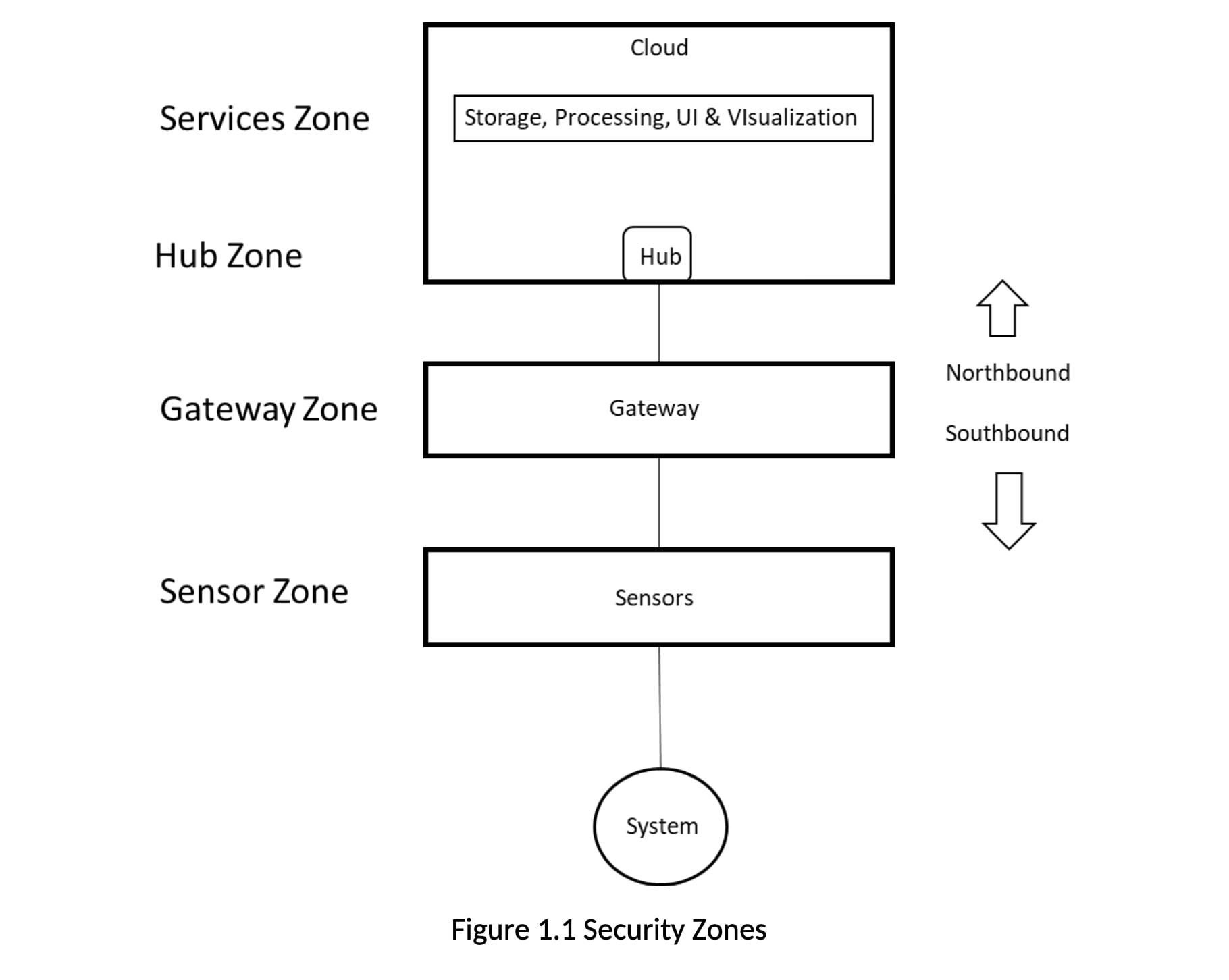
IIoT solutions must be trusted to provide data and information with integrity, as they are monitoring and measuring business critical systems and environments. That trust is verified by ensuring the system is secure against threats. Threat modeling is the best approach to designing for security. Using a typical IIoT solution configuration, we can identify several zones (Figure 1.0). The boundaries of these zones are where data and information transition from one solution element to another. Threats will be against the boundaries of these zones.
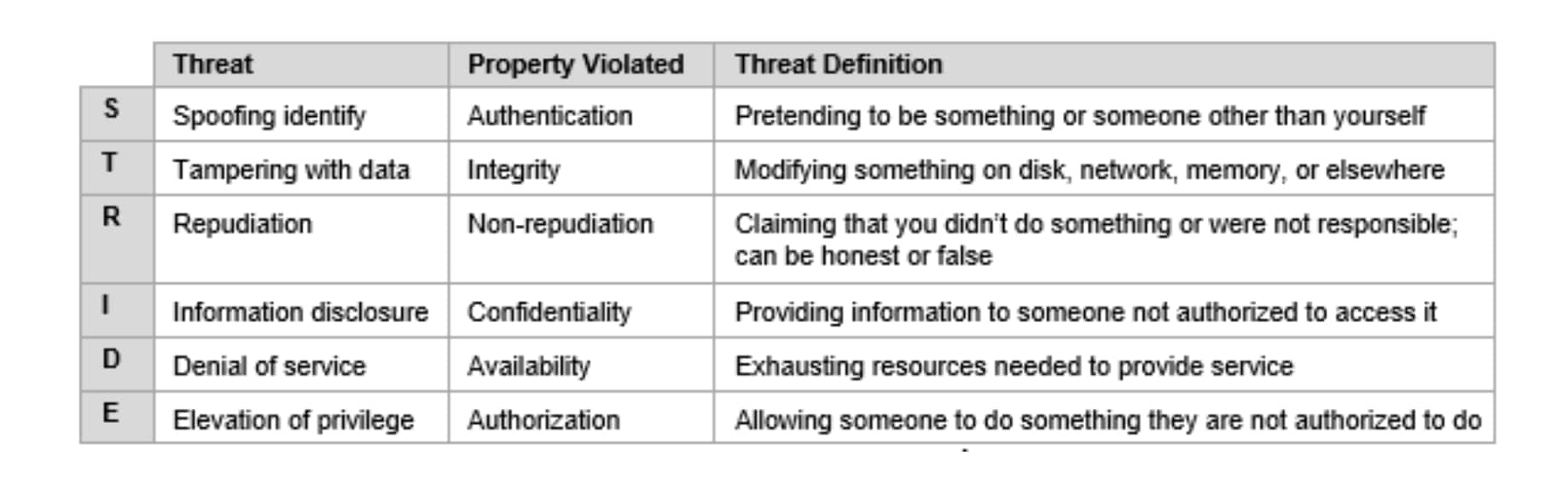
For the threat analysis we use the STRIDE model, which defines threats using the categories in the table below.
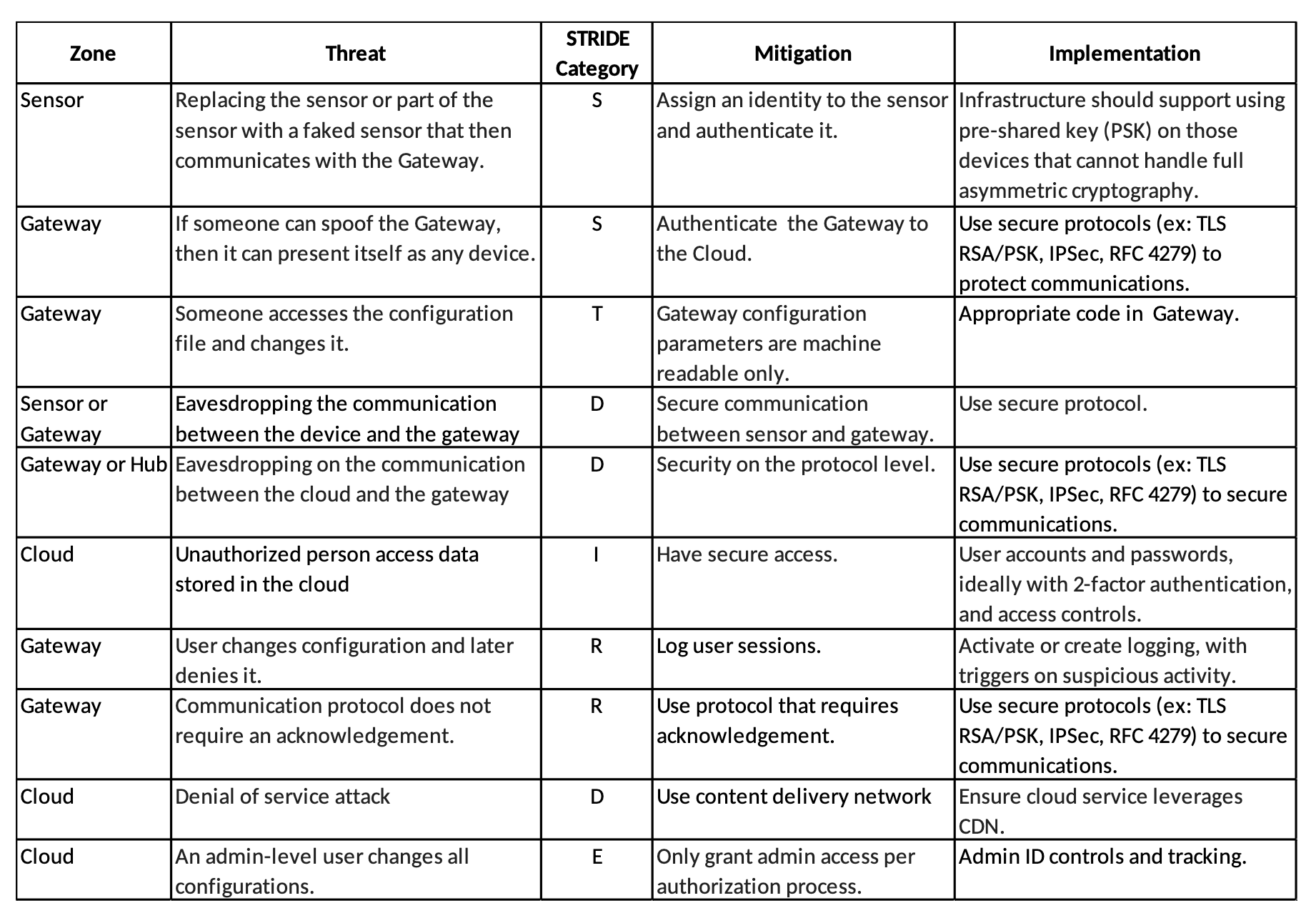
Applying the STRIDE model to the security zones identified above, we can generate a table similar to the one below. This is a simplified version of a much longer table that shows the security zone, the type of threat against it, and how that threat could be mitigated.
 SCHLIESSEN
SCHLIESSEN

